Here’s the Key to Navigating Post-Quantum Cryptography: Prepare, Don’t Panic
There’s no shortage of hype surrounding quantum computing – you could get caught up for days just talking about where quantum technologies are going, how they’re affecting us, and what they’ll be capable of in the future.
But the most important question security and business leaders must ask now is how will post-quantum cryptography impact cybersecurity?
Thinking about this question can easily induce panic and presumption, but there’s no need for that. There is, however, a need to prepare now. And fortunately, there are steps organizations can take today to get ready for Q Day, whenever it arrives.
 Looking Ahead to the Very Near, Very Real Quantum Future
Looking Ahead to the Very Near, Very Real Quantum Future
The number one question everybody has is “when is post quantum?” The answer, unfortunately, is that we just don’t know. But we do know that it’s real and that it’s coming.
Post-quantum computers exist today, but they’re not at the point where they can break the cryptographic algorithms we’re currently using. That said, they’re rapidly accelerating, and that day will come. And if the RSA 2048 algorithm, on which the entire world relies, is compromised by the near-term advancement of quantum computers, we’ll quickly find ourselves in a scenario where all encrypted sessions, TLS, server certificates, PKI, code signing, and more are under severe duress.
Consider the following graph from Quantum Amsterdam, which illustrates various timelines for a potential Q Day, or the moment when RSA cryptography can be broken in a matter of seconds and, therefore, would lend itself to a real time breach scenario. This is interesting because if we look at our assets within an organization and start to think about all the places where we use cryptography, we’ll very quickly come to realize just how vast it is.
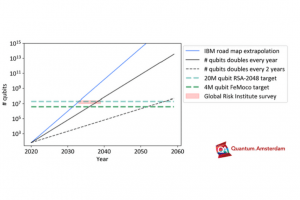 Critically, we need to get asymmetric cryptography under control, because regardless of Q Day timing, there are government requirements in the US that require post-quantum resistant signing to take place. We’re already in the final machinations of the NIST post-quantum algorithms, and by the end of 2023, new standards will be ratified that we can then implement in PKI and code signing. And we can expect that once the existing standard(s) falls, the next few will start to come into place fairly quickly.
Critically, we need to get asymmetric cryptography under control, because regardless of Q Day timing, there are government requirements in the US that require post-quantum resistant signing to take place. We’re already in the final machinations of the NIST post-quantum algorithms, and by the end of 2023, new standards will be ratified that we can then implement in PKI and code signing. And we can expect that once the existing standard(s) falls, the next few will start to come into place fairly quickly.
This shift also requires us to consider the crypto-agility that the rise of quantum computing will demand as we build devices with a long shelf-life. For example, do we want to replace every ECU (engine control units) in every car in three to five years’ time because post-quantum is here, or should we expect the vehicle we buy to have crypto-agility built into it? Even on the enterprise side, there’s a lot of valuable data that has a much longer shelf life than we might realize at first. Consider the case of biometric markers for your passport: Anything that’s EID enabled likely has information with a long shelf life.
Against this backdrop, it’s essential to start thinking about what post-quantum means for your organization and where the risk will lie in the short, medium, and long-term. You also need to consider how your organization will start making changes to get to a better state prior to Q Day.
Navigating Post-Quantum Cryptography is About Being Ready
Understanding the full scope of post-quantum cryptography is overwhelming for a lot of organizations, as most companies have cryptography built into places they don’t even realize. In fact, 62% of organizations don’t know exactly how many keys and certificates they have, which will make the ability to manage and mitigate risk incredibly difficult, even for large teams.
Knowing these blind spots are prevalent, it’s not surprising that many organizations expect the inventory discovery and planning phase – not even the actual implementation – of post-quantum to be a multi-year activity. That’s why now is the time to prepare.
Specifically, rather than preparing for a certain point in time, you need to prepare for the eventual need to adopt these new algorithms. And the sooner you can do that, the better off your organization will be.
It’s important to note that adopting these new algorithms is not just a flip of a switch; it’s a complete re-seeding of cryptography, with a whole new set of policies, operational procedures, and methodologies. For example, there are some pretty big key sizes involved in post-quantum that will make it more difficult for some devices to work. While there are several schemes being considered for overcoming some of these larger key sizes, it will create more overhead and cause problems for some of the traditional protocols being used. You need to take those changes into account and properly plan for them or you’ll end up with bottlenecks across the network.
This re-seeding will make the transition even more complicated than the last time we had a big change in cryptography, when SHA1 was deprecated in favor of SHA2. Last time around, we learned important lessons about managing roots of trust alongside key material and planning ahead to avoid inadvertently taking systems offline that will be essential to keep in mind.
What to Expect When Preparing for Post-Quantum Cryptography
Knowing the time to prepare for post-quantum cryptography is now, what does your organization need to do? Consider the following steps:
- Get to know your crypto: You cannot prepare unless you know your keys, certificates, and algorithms – and the apps that use them. There’s only one way that it’s going to be possible to address this whole scenario, and that’s by knowing your cryptography, understanding what’s in your organization, and identifying what can be migrated and what can’t be migrated. To help, Keyfactor has a tool available on our website where you can issue yourself post-quantum keys and see what can read them and what can’t. Until you get to know what that landscape is like in your organization, you cannot possibly develop a plan to do the migration because you can’t assess the risk, what needs to be replaced, what’s going to be compatible, and what needs upgrading.
- Lay the groundwork: Next, begin mapping where the biggest needs are and what teams you’ll need to work with. Most organizations will have a large, complex matrix of data, and you need to understand what data is valuable, which data has PII, and so on to identify areas of concern. Consider when you need to make changes in encryption for each data set, how you’ll do so, and the support you’ll get to make it happen. From there, it’s important to think about application compatibility and whether the algorithm change will break anything. Along the way, you’ll need to explore all your options, as it’s not just a one and done scenario.
- Explore your options: Algorithms will take a while to finalize, but it’s never too early to test and explore so you can get familiar with the things that need to happen. Think about potential scenarios that could happen: What if an algorithm is found vulnerable? How will you manage that post-deployment? Those dynamics will continue to exist in your organization, and they will need to be addressed downstream.
- Strengthen strategic partnerships: Organizations can’t successfully prepare for the shift to PQC in a vacuum – that’s where strategic partnerships come in. Seek out partners that allow you to test out their post-quantum solutions.
Building a Future-Proof Quantum Strategy
Post-quantum cryptography will affect everything we do, and adapting accordingly is inevitable.
Even in this new world, cryptography still sits at the center of security. Keys, encryption, digital signatures, and all the underlying technologies and fabric that we rely on today will remain important, but the algorithms behind them will need to change. That’s why organizations like NIST, X9, the CA Browser Forum, the IETF, and the National Cybersecurity Center of Excellence, are all working together to produce quantum-resistant algorithms.
If you haven’t already started to address this impending change in your organization, the time to do so is now. It all starts by understanding your cryptographic assets and preparing for the change in a highly agile way. It will be a big undertaking, as developing a post-quantum crypto-agility strategy takes a village, so the sooner you can assemble your team, find the resources you need, and start planning, the better.
Ready to get started? Check out Keyfactor’s PQC Lab — a place for IT leaders, security pros, and developers to learn, explore, and prepare for the post-quantum world.
Sponsored by Keyfactor. Authored by Chris Hickman at Keyfactor.
![]()





















