From Quantum Networks to the Quantum Internet
(Sponsored by IDQ; Authored by Bruno Huttner, Director of Strategic Quantum Initiatives at ID Quantique) Today, the quantum threat is well-understood. Small-scale quantum computers are already available. Most experts agree that large-scale quantum computers, which will be able to destroy the current cybersecurity infrastructure, will probably be ready within this decade. Fortunately, some solutions already exist while others are under development. They encompass both new algorithms (classical solutions) and the use of quantum technologies (quantum solutions) more specifically Quantum Key Distribution (QKD). The development of a quantum communication infrastructure will not only help secure our communications, but also offer new opportunities.
Early days: QKD links
In QKD, two distant users, known as Alice and Bob, exchange quantum objects, the qubits, through a quantum channel. With a proper protocol, quantum theory ensures that any attempt at eavesdropping on the channel results in a modification of the qubits, which will be detected by Alice and Bob during a processing stage. Therefore, QKD offers a secure way to exchange cryptographic keys. The main limitation of the scheme is that a qubit cannot be amplified, which means that QKD links are limited in distance. Commercial systems typically expand to one hundred kilometers. Academic experiments managed several hundreds.
The first practical implementations of QKD were offered to medium scale companies, who needed to secure links between two distant buildings, and between regional datacenters. QKD links were only point-to-point. The end-users had to own and operate their system, which restricted the scope of use. Longer distances and more complex topologies were needed.
Current architecture: Quantum Networks
Quantum Networks (QN’s) combine multiple QKD links into a single network. Users located at any node of the QN can ask the network to build end-to-end secure keys. The nodes of the QN, known as Trusted Nodes (TN’s), combine the secret keys from different QKD links. These nodes and the operators must therefore be trusted by the end users.
Today, all existing QN’s rely on the TN architecture. A few companies operate small scale QN’s, with a few nodes, mainly as testbeds. However, this is now changing. A QN extending over thousands of kilometers and hundreds of nodes have been built and are operated in China. A countrywide QN, which will secure government communications, is being built in South Korea, through a collaboration between ID Quantique and SK Broadband. The European Union is also planning a Quantum Communication Infrastructure, which will include both ground-based and space-based QKD, over the whole of Europe.
Next Gen Quantum Networks
A major hurdle delaying widespread adoption of QKD is the need for TNs in QNs. This constraint will be removed by the development of quantum repeaters. The nodes of these new QN’s will only be relays, which will transfer the qubits without measuring them. Quantum repeaters will provide end users with a high security level, without the need to trust intermediate nodes with the keys. We believe that this will happen during this decade.
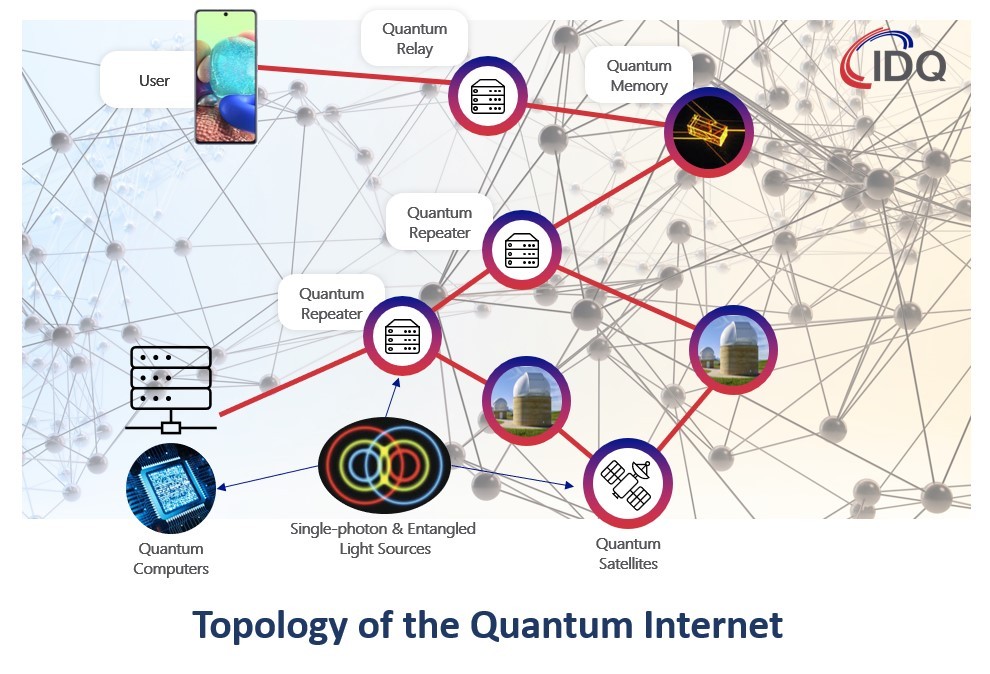
Towards the Quantum Internet
In QN’s, the quantum layer is only used for the transport of qubits. The end-product provided by the network are classical keys, used for security purposes. The next step is to go to full quantum and keep all the exchanges at the quantum level, including at the end nodes. At this point, the QN will not exchange keys, but rather offer a completely new service: entangled states. This will start at a local or regional level, but should evolve into a completely new network, the Quantum Internet.
Despite the current hype, the applications of the Quantum Internet are not yet well-defined. This should not really come as a surprise, as most applications of the (classical) Internet were also not forecasted. Currently, the most prominent idea is to use it for security. Users connected to the Quantum Internet could obtain keys, which secrecy could be directly tested. Improving the power of quantum computers by connecting them in a quantum network is also expected. Another intriguing idea is to build an earth-scale quantum sensor, for example for astrophysics. It is very likely that new applications will be forthcoming in the next few years.
At ID Quantique, we work with organisations of all types to help them plan for the quantum future. ID Quantique’s Quantum-Safe Security solutions work out-of-the-box with leading network encryption providers & services, making the path to quantum safety simpler than it may seem. Our new high-efficiency detectors will become bricks in the future Quantum Internet. Contact us today on info@idquantique.com or visit our website: www.idquantique.com.
More information on IDQ’s QKD technology here
























